Getting Started with Bluetooth Low Energy (BLE)
- 4 minutes read - 742 wordsIn a previous article, we explored how to build IoT firmware applications using the nRF Connect SDK. We examined its project structure and learned how to build and flash firmware on the nRF52840 dongle. If you missed it, you can catch up here:
For more hands-on practices, use nRF52840 Development Kit (DK), that offers advanced developer features. You need to connect this board via a high-speed data cable like this one, to get it detected on your PC. Follow the “Quick Start” guide from nRF Connect for Desktop, it enables you to test various SDK-provided samples, such as Bluetooth connectivity with a mobile device.
In this article, we’ll dive into Bluetooth connectivity in the IoT context and provide a concise overview of BLE fundamentals. For more details follow the course 🔗 BLE Fundamentals — Nordic Developer Academy
What is Bluetooth Low Energy (BLE)?
BLE is a Bluetooth protocol designed for low-power consumption, specifically for IoT devices. Introduced by the Bluetooth Special Interest Group (SIG) in Bluetooth Core Specification v4.0, BLE ensures that devices can operate efficiently while maintaining robust connectivity. For a product to use Bluetooth, it must be registered with SIG, making membership essential for manufacturers.
Key BLE Terminologies
Let’s now understand various terminologies of BLE protocol.
- Application Layer— The topmost layer of the BLE stack that manages application logic, user interactions, and various BLE profiles and services.
- Host Layer— This layer supports the Application Layer by encapsulating data storage and exchange for applications (L2CAP layer) and securing communication each other (Security Manager Protocol (SMP)). It define how organized into Attributes and Characteristics (ATT)
- Controller Layer — The foundation of BLE, managing data modulation on the physical radio (PHY layer) and connection states (Link Layer).
- Advertising —Peripheral devices broadcast data packets to announce their presence to Central devices.
- Scanning — Central devices discover Peripheral devices through scanning. Connections can then be initiated as needed.
- Network Topology — A device can act as central as well peripheral. Central is generally a resource consuming device like mobile phone/laptop but peripheral can be low resource device. Connection between contral and peripheral is many to many.
- Generic Attribute Profile(GATT) — Once a connect is made, Data exchange follows a client-server model. Where GATT server (peripheral device) stores data in Attributes defined by Characteristics of some Service, a set of services get exposed under a Profile, that are further discovered and accessed/polled by GATT Client(Central device).
- BLE Connection — Data can be broadcasted and listens without a continuous connection, however “pairing” can be used for establishing secure communication. “Bonding” for encrypting future reconnections.
BLE Implementation in nRF Connect SDK
The nRF Connect SDK is a versatile framework for developing low-power wireless applications using Nordic Semiconductor devices. For BLE, it provides it SoftDevice Controller and Zephyr Bluetooth Host for BLE Stack
Developing BLE Firmware
The BLE Fundamentals course by Nordic Developer Academy offers practical exercises using the nRF Connect SDK and VS Code. Key exercises include:
- Advertising Packets (Beacons): Writing code to broadcast data packets where first two bytes is SIG approved manufacturer identifiers.
- Peripheral Device Development: Setting up the nRF52840 DK as a peripheral device.
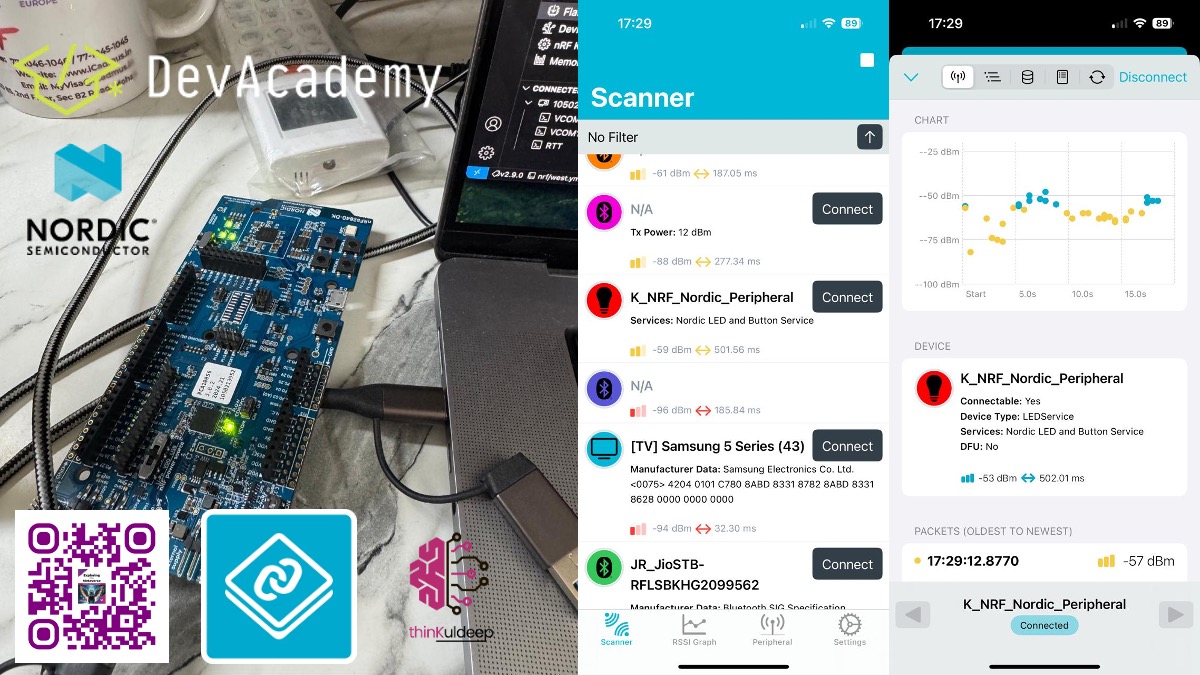
- Scanning and Connection: Using the nRF Connect for Mobile app to detect broadcasts, make connections, and explore GATT services.
- UART Communication and Security: Implementing secure data exchange with features like: Filter Accept Lists, Pairing (e.g., unauthenticated or authenticated pairing)
BLE Security Levels
Security is very subjective in BLE, It depends heavily on how the pairing process is executed and what I/O capabilities the peer devices have. Here are level of security
- Level 1: No security (open text, meaning no authentication and no encryption)
- Level 2: Encryption with unauthenticated pairing
- Level 3: Authenticated pairing with encryption
- Level 4: Authenticated LE Secure Connections pairing with encryption
Sniffing BLE Data
Similar to web traffic analysis with Wireshark, BLE traffic can be sniffed using nRF Sniffer for BLE. Steps include:
- nRF Sniffer Hardware — Flash nRF Sniffer firmware to an additional nRF52840 DK or dongle.
- Wireshark with external capture — Use the Nordic sniffer plugin with Wireshark to capture BLE packets.
- Place the Sniffer in between Peripheral and Central device.
- Analyze the data to understand BLE interactions.
What’s Next?
This article provides a foundational understanding of BLE. To deepen your knowledge, hands-on practice is essential. Explore the BLE Fundamentals course by Nordic Developer Academy to build, test, and master BLE applications.
Stay tuned!
Keep sharing, Keep Learning!
Find the IoT Practices Publication for more details.
#IOT #network #cloud #getting started #learning #technology #fundamentals #ble #nRF #SDK